
Stay Protected with Managed Cybersecurity Services
Cyberattacks are among the most serious threats that businesses today are facing. As technology evolves, so do these online threats that target businesses of all

Cyberattacks are among the most serious threats that businesses today are facing. As technology evolves, so do these online threats that target businesses of all

When people work from home, their daily physical activity often decreases. Unlike commuting to work and walking around the office, home-based work tends to involve

One essential tool that often gets overshadowed, but has a surprisingly big impact on your daily tech interactions, is your trusty mouse. Whether you’re a
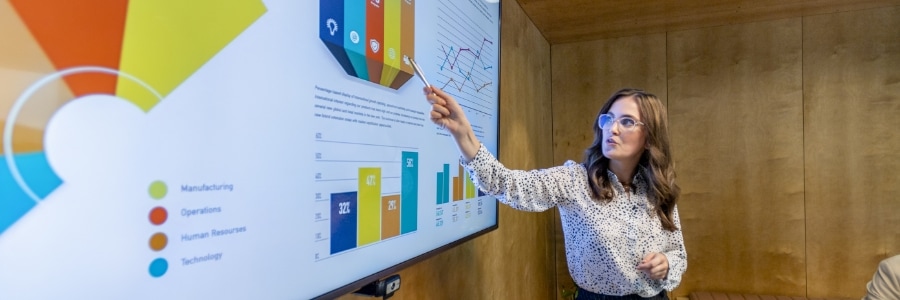
Giving a PowerPoint presentation doesn’t have to be a daunting task with the right tools. PowerPoint Presenter Coach is one such tool that’s designed to

Managed Cloud Services have been the buzzword in business for the past decade. They provide a practical answer to several business concerns like data storage,

The world of business communication is rapidly transforming, and staying ahead requires embracing technologies that can grow with you. Voice over Internet Protocol (VoIP) offers

Productivity is a major issue in the workplace due to such things as information overload and time-consuming tasks. Fortunately, there are easily available tools in

The success of any business relies heavily on efficiency. Early on, it’s easy to keep operations efficient, especially when the organization is small. However, as

Investing in new technology is a powerful way to drive business growth. Whether you’re purchasing new servers to boost productivity or subscribing to a project
"*" indicates required fields